Is your organization serious about the security of third-party dependencies? Do you get questions from your CISO/SecOps team about open-source health? Does the complexity of your application landscape make it difficult to understand which modules, widgets, java libraries are used where? Then, keep reading!
Mendix is proud to announce Software Composition, a newly released capability that provides an accurate inventory of application and application landscape component dependencies. Software Composition is a fundamental building block to improve your security posture.
Anatomy of a Mendix Application
Let’s start with the basics. A Mendix maker creates pages, domain models, microflows, nanoflows, custom modules and more to build a Mendix app. This is called the Mendix Model. The Mendix Model can be extended with custom java and java script if needed. All these are built by the application maker and are marked in black color in the illustration below.
When custom Java or JavaScript is used to extend the Mendix Model, Java libraries and npm packages can be added to the Mendix application. Pre-built, re-usable components such as modules and widgets from the Mendix Marketplace can also be used to super-charge your application. Lastly, the right Mendix Runtime version will help run the application. All these are third-party dependencies are illustrated in blue color below. These third-party dependencies can be maintained by Mendix, its community or its partners.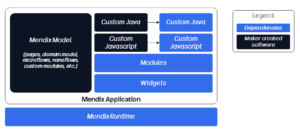
Challenge
Over time, third-party dependencies may become deprecated, outdated, vulnerable or unpreferred, depending on your enterprise quality and security rules. Hence, visibility into these third-party dependencies is key to effectively managing the quality and security of your application landscape.
This need becomes more pronounced as the number of applications in the landscape increases. A central place to view application landscape components becomes vital to manage landscape security risk.
Introducing Software Composition
To enable this visibility, Mendix will generate a software bill of materials (SBOM). An SBOM is a .json file created in the Cyclone DX format that summarizes the third-party dependencies used in software. The SBOM will consist of standard marketplace modules, widgets, java libraries, npm libraries and runtime version, depending on the supporting Studio Pro version. SBOMs can be generated using MxBuild.
Mendix will automatically generate SBOMs under the hood for new deployment packages with Studio Pro versions 9.24.22 and above, 10.6.9 and above, and 10.10.0 and above for free cloud, public cloud and cloud-dedicated deployment models and make these available for download.
But don’t worry, you don’t need to parse .json files to get visibility. You can easily view the SBOM contents on the Software Composition page in Control Center and Developer Portal in an easy-to-consume manner. In Control Center, software composition visibility is across the entire application landscape. In Developer Portal, visibility is for each application.
On the Software Composition page in Control Center, you can do the following:
- View the Software Composition of each application environment
- Download the SBOM or export via excel
- View a list of all unique components used in your application landscape. For each component, it’s also possible to view the number of applications and environments using it.
Get started now!
Excited? Here are some practical tips to get started.
Ensure you meet the pre-requisites
Software Composition visibility is available for 9.24.22 and above, 10.6.9 and above, and 10.10.0 and above for free cloud, public cloud, and cloud-dedicated deployment models. Newly created deployment packages will have SBOMs and related visibility on the Software Composition page. To get Software Composition visibility, ensure that you upgrade your Studio Pro as needed and create new deployment packages.
Check for vulnerabilities and determine their impact radius
Mendix publishes security advisories for its components. Check the All Components tab on the Software Composition page to see if you’re using a vulnerable component and to identify its impact radius.
For instance, we issued security advisory CVE-2023-27464 (with a score of 5.3 out of 10) for the Forgot Password module. On the All Components tab you can determine the number of apps that use the Forgot Password module. You can also see additional details on consuming apps, such as application names, environments affected, technical contact, etc. Use this information to analyze the vulnerability’s impact radius. Then advise impacted teams to take the remediation actions listed in the security advisory.
Monitor adherence to your quality and security guidelines
You may have enterprise guidelines around which components to use. (For example, components that use a disallowed license type shouldn’t be used). Gaining visibility into your application and application landscape inventory is a first step to checking for compliance with such rules.
So don’t wait, get started now and manage security risk with ease. Raise awareness about the release of Software Composition to gain a true understanding of your software composition inventory!
- 3 Reasons You Need to Rethink Low-Code Governance
- Mendix Solutions Kit Delivers Adaptable Solutions to Software Vendors
- Empowering Innovation: The Dynamic Duo of Teamcenter and Mendix
- What is Technical Debt? Examples, Prevention & Best Practices
- Cloud-Native Applications: Examples, Benefits and Development Methods